Web Application Security Testing Method
Hunt Bugs ! Test Vulnerabilities !

Hi there, I’m Sakib Haque Zisan — Engineer | Pentester | Entrepreneur | Cyber Security Instructor
It has always been my Passion to learn new things, explore new ideas and thoughts and emphasized on self-development. It has always been my focus on every available opportunity to improve myself skills. I want to pursue my goals with dedication, sincerity, honesty and hard work.
Today I will discuss How I test vulnerabilities of a Target Website and what is my Methodology. So Let’s START !!
Web Application Security Testing Method
Methodology:
Recon
- Footprinting Website [ Recon with OSINT ]
- Recon with Browser Addons [ Finding Technology, Service information ]
- Google Dorking
- Github Dorking
- Port Scanning
- Finding DNS Information
- Whois Lookup
- WAF Identification
- Shodan Dorking
Enumeration
- Check Security Header Info
- Subdomain Enumeration
- Filtering Live Domains
- URL Extraction
- Content Discovery
- Finding Parameters
- Sorting URLs
Vulnerability Scanning
- Automation in Vulnerability Scanning
- Scan Vulnerabilities manually through the testing methods of OWASP Top 10 Vulnerabilities Category.
- Analyze Vulnerabilities Database.
So Now Let’s Start the Journey to find out the Bugs in our Target Website !!
Step 01 —
Footprinting Website
First of all, I would like to footprint my Target website through some reputed methods and Techniques !!
- Finding the Target Website’s IP through Website to IP lookup. [ Recommending https://www.nslookup.io/ ]
- Finding out the X-Ray Vision for my Target Website [ Recommending https://web-check.as93.net/ ]
- Finding the Geographical Location of the Target [ Tools — Google Earth, Google Maps, Wikimapia ]
- Gathering information from Financial Services [ Tools — Google Finance, MSN Money, Yahoo! Finance ]
- Gathering Information from Business Profile Sites [ Tools — Crunchbase, opencorporates, corporationwiki ]
- Monitoring Target using Alerts [ Tools — Google Alerts, Twitter Alerts. Giga Alerts ]
- Tracking the Online Reputation of the Target [ Tools — Mention, ReviewPush, Reputology ]
- Gathering Information from Groups, Forums and Blogs
- Gathering Information from Public Source Code Repositories [ Tools — Recon-ng
- Footprinting through Social Networking Sites. [ Facebook, Twitter, Linkedin etc ]
- Collecting Information through Social Engineering [ Collect information about the users and employees interest , cookies, sensitive information ]
- Analyze the Directory Structure of the Target Website [ Tools — Httrack ]
- Find out the Archive and Analyze previous data [ Tools — ViewDns, https://web.archive.org ]
- Extracting Meta Data of the Public Documents [ Tools — Exitfool, Web Data Extractor, Metagoofil ]
- Extracting Website Links [ Tools — CeWL ]
- Email Footprinting [ Tools — Infoga, eMailTracker Pro ]
Step 02 —
Recon with Browser Addons
Now Let’s Recon our Target Website through some Browser Addons !!
- Finding the Technology which are used to build our Target Website [ Tools — Wappalyzer, BuiltWith ]
- Detect the use of JavaScript libraries with known vulnerabilities [ Tools — Retire.js ]
- Gather Information of Ports, Services and Server and Common Vulnerabilities [ Tools — Shodan ]
- Test Web Application [ Tools — Knoxx , HackTools ]
Step 03—
Google Dorking
site:target.com -site www.target.com
Online Resource:
– https://github.com/chr3st5an/Google-Dorking
— https://www.stationx.net/how-to-google-dork-a-specific-website/
Step 04 —
Github Dorking
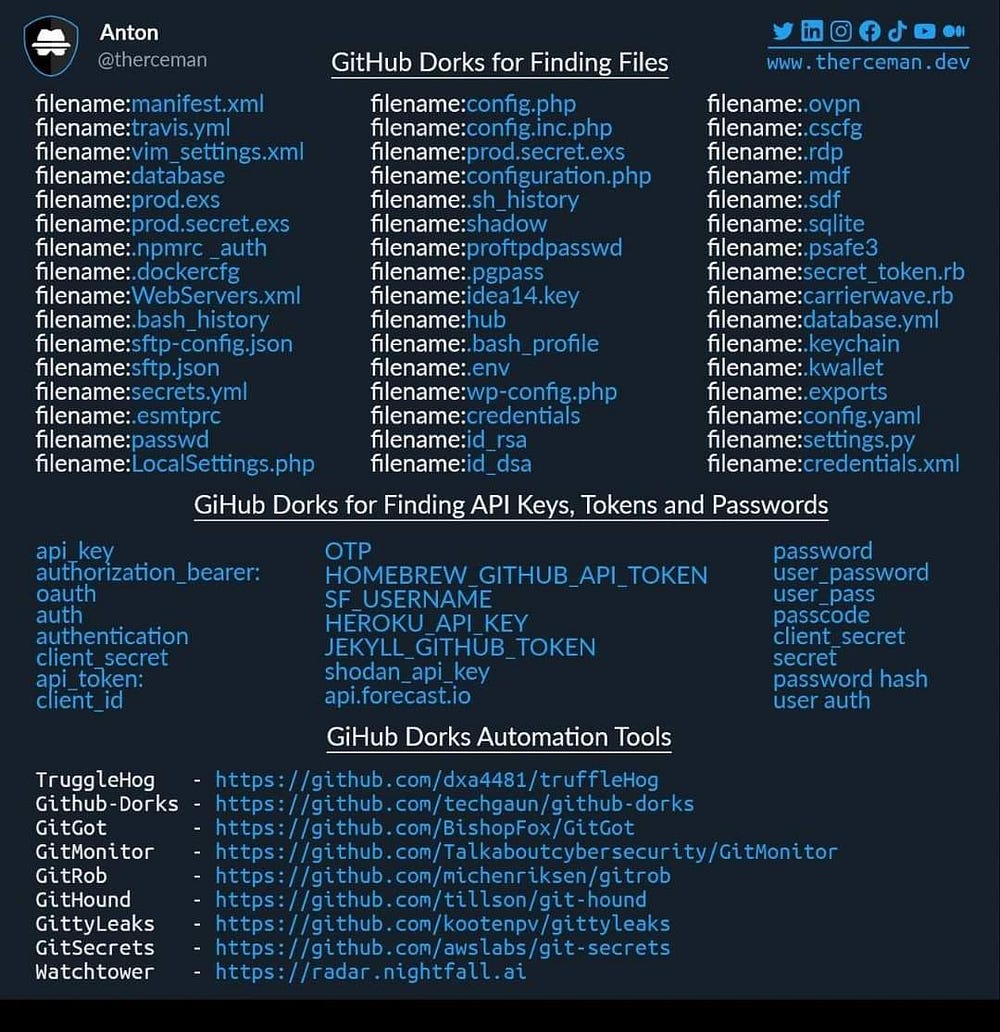
What you can find on Github?
• FTP Credentials
• Secret Keys [API_key, Aws_secret key, etc.]
• Internal credentials [Employee credentials]
• API Endpoints
• Domain Patterns
- Go to github and search
Eg.
- “target.com” “dev”
- “dev.target.com”
- “target.com” API_key
- “target.com” password
- “api.target.com”
Step 05—
Port Scanning
Now Let’s Scan the Ports of our Target Website through some necessary tools so that we can find out the way of Attacking !! Haha..
Tools in Scanning Ports —
- Nmap [ https://www.stationx.net/nmap-cheat-sheet/ ]
- UnicornScan [ https://0xsp.com/offensive/offensive-cheatsheet/ ]
- Angry IP Scan [ https://0xsp.com/offensive/offensive-cheatsheet/ ]
- Netcat [ https://0xsp.com/offensive/offensive-cheatsheet/ ]

Step 06 —
Finding DNS Information
Tools in finding DNS Information —
- Dig [ https://sid4hack.medium.com/decoding-dns-penetration-testers-journey-with-dig-7cb9845e6215 ]
- DNS Lookup
- MxToolbox
- Nslookup
- Viewdns

Step 07 —
Whois Lookup
Find out the Domain’s Information by using Whois Lookup. Link — https://www.whois.com/whois/
Step 08—
WAF Identification
In this case we need to identify our Target website is WAF Protected or Not. That’s why can use 2 different tools to complete the same task.
- Wafw00f [ https://github.com/EnableSecurity/wafw00f ]
- WhatWaf [ https://github.com/Ekultek/WhatWaf ]
Step 09 —
Shodan Dorking
Shodan is a search engine for Internet-connected devices. It is different from search engines like Google and Bing because Google and Bing are great for finding websites but Shodan helps in finding different things like popular versions of Microsoft IIS, control servers for Malware, how many host are affected with the new CVEs, which countries are becoming more connected, SSL certificates of the websites etc.
How to use CLI Based version (Basics) ?
I would like to suggest — Follow this Tutorial https://youtu.be/v2EdwgX72PQ?si=BedrWedKxxuy3cSk
Step 10 —
Check Security Header Info
HTTP Security Response Headers Cheat Sheet — https://cheatsheetseries.owasp.org/cheatsheets/HTTP_Headers_Cheat_Sheet.html
Step 11 —
Subdomain Enumeration
Let’s discuss the top 10 subdomain search tools that can help you discover subdomains.
- Sublist3r [ Python tool that leverages multiple search engines to enumerate subdomains for a given domain. ]
- Amass [ Open-source tool for passive reconnaissance that discovers subdomains, IP addresses, and other related information. ]
- Subfinder [ Subdomain discovery tool that uses multiple sources, including search engines and certificate transparency logs. ]
- Censys [ A search engine that provides access to a large and up-to-date database of internet hosts, including subdomains. ]
- Assetnote [ A tool for asset discovery and monitoring, helping with subdomain identification and tracking changes over time. ]
- Findomain [ Cross-platform subdomain enumerator that uses various sources to identify subdomains. ]
- SecurityTrails [ Offers a comprehensive DNS database to discover subdomains, IP histories, and other related information. ]
- Knockpy [ Python tool that uses multiple sources to gather subdomain information for a target domain. ]
- DNSDumpster [ An online tool that provides DNS reconnaissance services, including subdomain discovery. ]
- Aquatone [ A tool that helps visualize and gather information about domains, including subdomains, by combining techniques like screenshotting. ]
Step 12—
Filtering Live Domains
There is a tool called HTTPX, which is used to check Subdomains are Active or Not and there are multiple methods to use this tool. We will see the simple method only.
▶ Enumerate/Collect all subdomains using tools like subfinder, assetfinder, Knockpy and haktrails, etc.
Run : subfinder -d someweb.com -o subf.txt -v
Run : echo “someweb.com” | haktrails subdomains > haksubs.txt
Run : assetfinder -subs-only someweb.com > asset.txt
▶ Add all Enumerated/Collected subdomains from different tools in different files into one file with unique subdomains, that may be subdomains.txt
Run : cat subf.txt haksubs.txt asset.txt | sort -u > subdomains.txt
▶ Now, will check the identified subdomains are active or not -
Run : httpx -l subdomains.txt -o activesubs.txt -threads 200 -status-code -follow-redirects
▶ You’ll able to see the active subdomains only, on which you can start finding bugs and all.
***Another Tools is Reconftw
Step 13—
URL Extraction
Here are some useful tools to perform this method —
- Httpx
- WaybackURLs
Step 14—
Content Discovery
Here are some useful tools to perform this method —
- Httpx
- Gobuster
- Dirbuster
Step 15—
Finding Parameters
We are going to enumerate a web application to find out hidden parameters of the Target website,
Here are some useful tools to perform this method —
- Arjun Tool
- ParamSpider
- WaybackURL
Step 16—
Sorting URLs
GF tool is a powerful command-line utility that acts as a wrapper around the grep command, providing additional functionality and convenience for searching and filtering text.
Link — https://github.com/tomnomnom/gf
Step 17—
Automation in Vulnerability Scanning
- Nessus — Nessus is a remote security scanning tool, which scans a computer and raises an alert if it discovers any vulnerabilities that malicious hackers could use to gain access to any computer you have connected to a network.
Using Process — https://youtu.be/Gy-aPBb0djk?si=OsjRy9uiPXt_oTT6
2. Burpsuite — Burp Suite is an integrated platform/graphical tool for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.
Using Process — https://www.youtube.com/watch?v=hY_gzrTMn3U&list=PLwO5-rumi8A7TVRzfOD4OHabwJ0v1ZA81
3. ZAP — OWASP ZAP is a penetration testing tool that helps developers and security professionals detect and find vulnerabilities in web applications.
Using Process — https://www.youtube.com/watch?v=bf2YuqgaeWo&list=PLH8n_ayg-60J9i3nsLybper-DR3zJw6Z5
4. Acunetix — Acunetix is an automated web application security testing tool that audits your web applications by checking for vulnerabilities like SQL Injection, Cross-site scripting, and other exploitable vulnerabilities.
Using Process — https://darkyolks.medium.com/vulnweb-lab-report-an-analysis-of-vulnerabilities-on-the-web-c33472761913
5. SQLmap — SQLMAP is an open-source penetration tool. SQLMAP allows you to automate the process of identifying and then exploiting SQL injection flaws and subsequently taking control of the database servers. In addition, SQLMAP comes with a detection engine that includes advanced features to support penetration testing.
Using Process — https://www.youtube.com/watch?v=nVj8MUKkzQk&list=PL_jb7LxOF7HVvkuovEnszsWayU_-NOtxx
6. WPScan — WPScan is an open-source WordPress security scanner. It is used to scan WordPress websites for known vulnerabilities within the WordPress core and WordPress plugins and themes. It also checks for weak passwords, exposed files, and much more. Since it is a WordPress black box scanner, it mimics an actual attacker
Using Process — https://youtu.be/zmK_hg6hIM0?si=jU9GSnO6vl8hnmSN
Step 18 —
Scan Vulnerabilities manually through the testing methods of OWASP Top 10 Vulnerabilities Category.
First of all let’s talk about the Category and Sub categories of the OWASP Top 10 Vulnerabilities because if you know what are the bugs, then you can exploit those through your own methodologies of Testing.
OWASP Top 10 2021 — Bug Name Examples by Category:
A01: Broken Access Control
IDOR
Directory or Path Traversal
Function Injection
Privilege Escalation
Horizontal and Vertical Privilege Escalation
A02: Cryptographic Failures
Cleartext Transmission of Sensitive Data
Insufficient Entropy
Insecure Random Number Generation
Padding Oracle Attack
Use of Weak Ciphers
Weak or Misconfigured Cryptographic Configurations
A03: Injection
Os Command Injection
SQL Injection
Cross-Site Scripting (XSS)
Expression Language Injection
XML Injection
LDAP Injection
NoSQL Injection
SSTI
A04: Insecure Design
Security-by-Obscurity
Session Fixation
Unintended Functionality
Use of Hardcoded Credentials
Weak Error Handling
A05: Security Misconfiguration
Default Accounts and Passwords
Default or Weak Configuration Settings
Disabled Security Features
Improperly Configured Permissions and Access Controls (Insecure Permissions)
Unnecessary Features or Services Enabled
Use of Vulnerable Software
Directory Listing Enabled
Insecure Default Passwords or Credentials
Improperly Configured Cross-Origin Resource Sharing (CORS)
A06: Vulnerable and Outdated Components
Use of Known Vulnerable Components
Outdated Libraries and Frameworks
Third-Party Components with Unpatched Vulnerabilities
Lack of Patching and Updates
A07: Identification and Authentication Failures
Brute-Force Attacks
Credential Stuffing
Credential Theft
Session Hijacking
Weak Password Policies
Weak Session Cookies
Lack of Multi-Factor Authentication (MFA)
Insecure Session Management
Insecure Authentication Protocols
Insecure Password Storage
User Enumeration
A08: Software and Data Integrity Failures
Insecure Direct Object References (IDOR)
Server-Side Request Forgery (SSRF)
SQL Injection and NoSQL Injection Variants
Tampering with Updates
Unvalidated Redirects and Forwards
A09: Security Logging and Monitoring Failures
Lack of Audit Logging
Insufficient Log Data
Unmonitored Logs
Unsecured Logs
A10: Server-Side Request Forgery (SSRF)
Unauthenticated SSRF
Authenticated SSRF
Now you can test your Target website with several techniques to find out the vulnerabilities. Recommending to follow the related writeups of the vulnerability.
Step 19—
Analyze Vulnerabilities Database.
Recommending some resources —
- Exploit Database — https://www.exploit-db.com/
- Vulnerability Database — https://vuldb.com/
- CVE Security Vulnerability — https://www.cvedetails.com/
- Patchstack — https://patchstack.com/database/
Step 20—
Report Writing
Report Structure:
A security testing report should have a clear and logical structure. Here’s a recommended structure:
a. Introduction: Provide a brief overview of the security testing context, objectives, and report scope.
b. Methodology: Describe the techniques and tools used to conduct the security testing.
c. Findings: Present the identified vulnerabilities in a clear and organized manner. Use categories or severity levels to aid readability.
d. Evidence: Include screenshots, code snippets, or any other evidence to support your findings.
e. Recommendations: Propose specific corrective measures for each identified vulnerability.
f. Conclusion: Summarize the key points of the report and express gratitude to relevant parties.
Recommending to Follow this way too — https://www.intigriti.com/hackademy/how-to-write-a-good-report



0 Comments