IoT Hacking 101
Remember, if the question is IoT devices related then always use the mqtt protocol to analyze that packet.
An attacker had sent a message 166.150.247.183/US to the Victim. You are assigned to perform footprinting using shodan.io in order to identify whether the message belongs to SCADA/ICS/IoT systems in US
Just search the IP 166.150.247.183/US in shodan.io and then read out the information where it will find the message belongs to IoT and that is the answer.
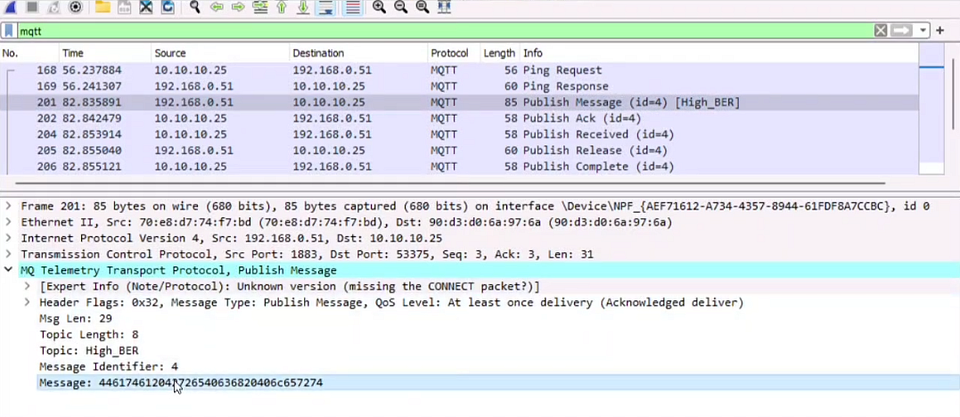
BCAPORG hosts multiple IoT devices and Sensors to manage its supply chain feet. You are assigned a task to examine the file “IOT Traffic.pacpng” located in the home directory of the root user in the Linux machine. Analyze the packet and find the topic of the message sent to the sensor.
Step 01: Run the wireshark tool and open the file from the instructed directory where file name is “IOT Traffic.pacpng”
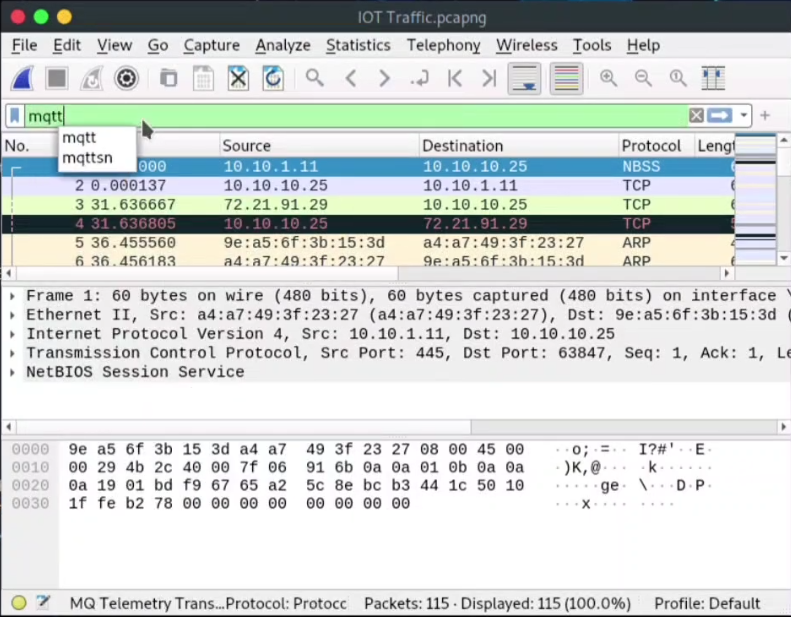
Step 02: Remember, if the question is IoT devices related then always use the mqtt protocol to analyze that packet.
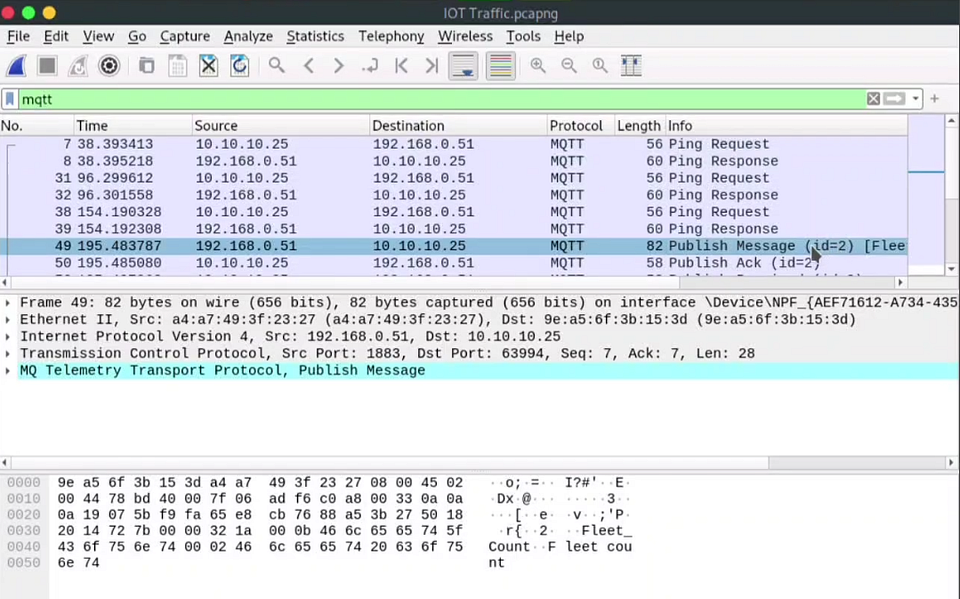
Step 03: Now we have to find the published message to analyze the packet and find the topic of the message sent to the sensor.
BCAPORG hosts multiple IoT devices and Sensors to manage its IT department. You are assigned a task to examine the file “NetworkNs_Traffic.pcapng” located in the home directory of the user in the Linux machine. Analyze the packet and find the alert message sent to the sensor.
Step 01: Run the wireshark tool and open the file from the instructed directory where file name is “NetworkNs_Traffic.pcapng”

Step 02: Remember, if the question is IoT devices related then always use the mqtt protocol to analyze that packet.

Step 03: Now we have to find the published message to analyze the packet and find the topic of the message sent to the sensor.

Step 04: Now Click on the MQ Telemetry Transport Protocol option in the below and read the message
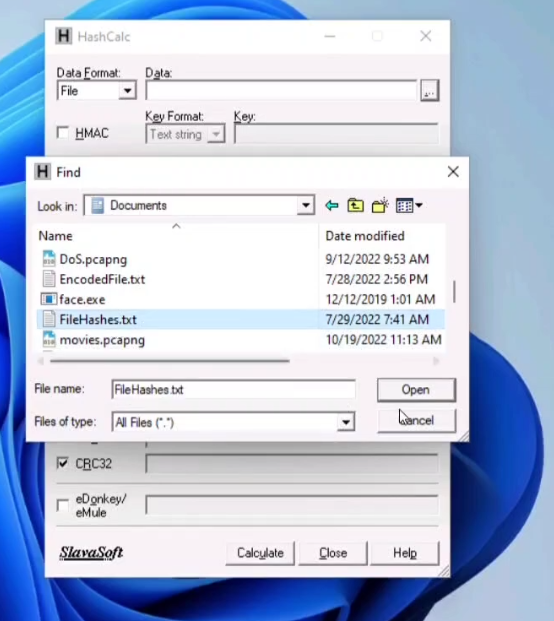
You have received a folder named “Archive” from a vendor. You suspect that someone might have tempered with the files during transmissions. The original hashes of the file has been sent by the sender separately and are stored in a file named “FileHashes.txt” stored in the Document folder 0f the Windows Machine. Your task is to check the integrity of the files by comparing the MD5 Hashes. Compare the Hash values and determine the file name that has been tempered with. Note: Exclude the file extension in the answer field. The answer is case sensitive
Step 01: Run the Tool “HashCalc”
Step 02: Select the Data option for choosing file to open with HashCalc
Step 03: Select the MD5 option and uncheck others. And then select Calculate to find the answer.
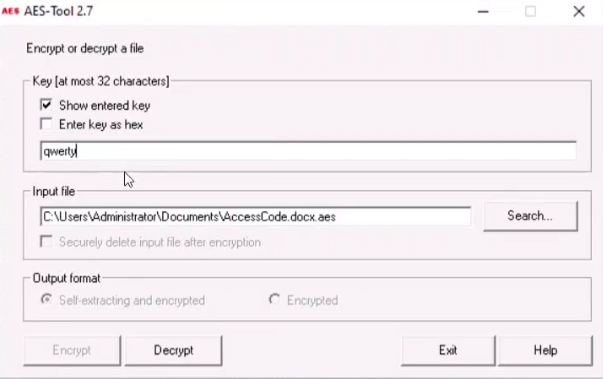
The Access code of an employee was stolen from the BCAPORG database. The attacker has encrypted the file using the advance encryption package. you have been assigned a task to decrypt the file; the organization has retained the cipher file “AccessCode.docx.aes” in the Document folder of Windows machine. Determine the access code by decrypting the file. [Hint: Use “querty” as the decryption password.
Step 01: Run the Tool “AES Tool” or double click on the file “AccessCode.docx.aes” in the Document folder of Windows machine to automatically run with the tool.
Step 02: Uncheck the “Enter Key as Hex” option and enter “querty” as the decryption password
Step 03: Then choose the Decrypt option below and save the doc file and open it . There is the answer.
An attacker has intruded into the BCAPORG with malicious intent. He has identified a vulnerability in a machine. He has encoded the machine’s IP address and left it in the database. While auditing the database, the encoded file was identified by the database admin. Decode the EncodedFile.txt in the Document folder in the and Enter the IP address as the answer. [ Hint: Password to decode the file is P@$$w0rd ]
Here we have to use the Tool BCTextEncoder
Step 01: After running the app, choose to Decode the EncodedFile.txt file
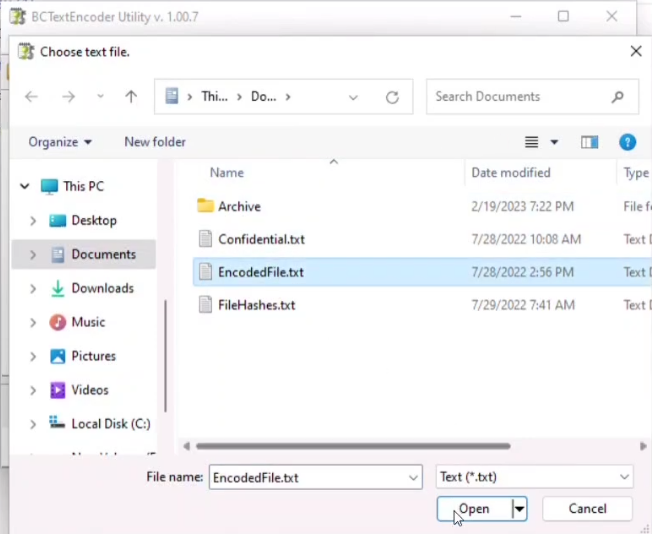
Step 02: Type P@$$w0rd to decode the Password and then click Okay button.
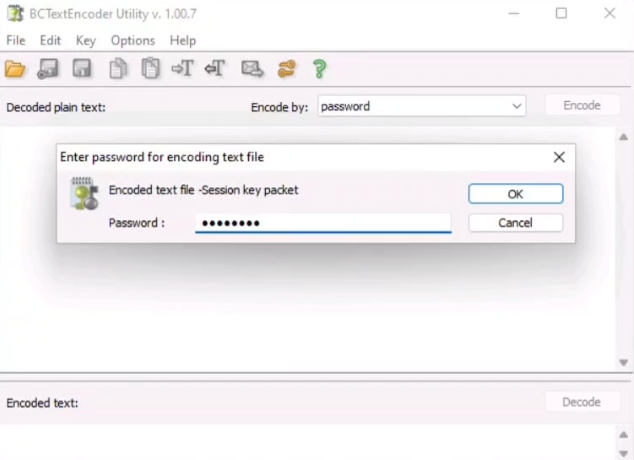
Step 03: Then there you will find the answer.
A VeraCrypt volume file “secret” is stored on the Document folder in the Windows machine. You are an Ethical hacker working with BCAPORG; you have been tasked to Decrypt the Encrypted volume and determine the number of files stored in the volume. [ Hint: Password:test ]
Step 01: Double click on the file “secret” in the Document folder of Windows machine to automatically run with the tool VeraCrypt.
Step 02: Enter there the Password is test
Step 03: Once you enter the password and click on the Dismount option to track the total number of files stored in the volume and that is the Answer!!
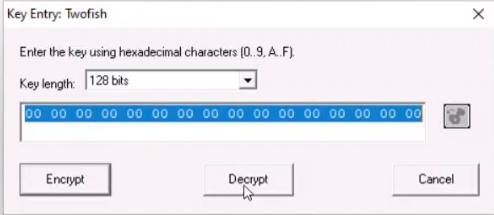
An attacker had sent a file cryt-128–06encr.hex containing ransom file password, which is located in Document folder in Windows machine. You are assigned a task to decrypt the file using Crypt Tool. Perform cryptanalysis, identify the algorithm used for the encryption and hidden text. [ Note- Check filename for key length and hex characters]
Step 01: Run the tool Crypt Tool
Step 02: Open the file cryt-128–06encr.hex containing ransom file password, which is located in Document folder in Windows machine.
Step 03: Follow the Steps — Select Encrypt / Decrypt option from the menu bar > then select Symmetric Modem > then select Further Algorithms > then select Twofish
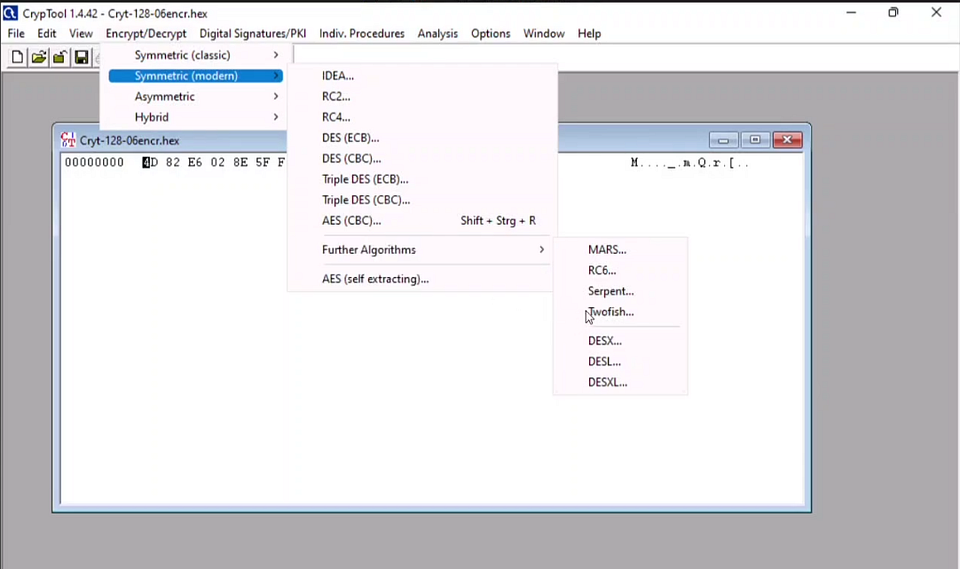
Step 04: Then select Decrypt button and that is the answer.




0 Comments